Cybercrime
网络犯罪代考 The figure above shows the infiltrated infrastructure of the botnet. What did theresearchers do, and what impact did it have on the spam campaign?
1.Spam 网络犯罪代考
Kanich et al. managed to infiltrate the Storm botnet and conduct a measurement study of spam.
a.How was the storm botnet organised? How did bots communicate with the Mastera servers?
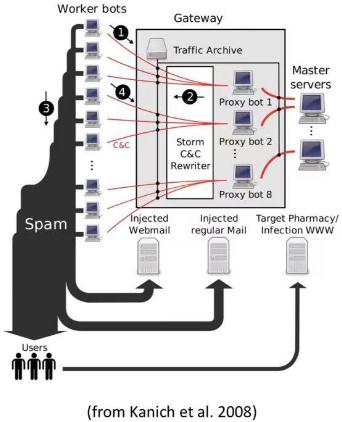
b.The figure above shows the infiltrated infrastructure of the botnet. What did theresearchers do, and what impact did it have on the spam campaign?[8 marks]
c.What data does this setup allow the researchers to collect?[5 marks]
d.What are some of the difficulties the researchers may encounter?(4 marks)
e.Discuss the ethical implications of this research. [5 marks]

2.Malware 网络犯罪代考
Consider the following brief description of a cybercriminal operation (source withheld):
ZendNudeZ is contained within seemingly legitimate, repackaged, Android apps, given away for freeon non-official markets. Once executed, the malware exfiltrates photos from the victim’s phone via abotnet to the criminal’s server and uses algorithms and DeepFakes technology to either identify, orcreate, compromising photos of the victim. These images are then used to demand a ransom as thecriminals threaten to release the photos to all of the victim’s contacts should they fail to pay.
For each victim, a Bitcoin payment address is created to control payment and automate a response.From those accounts, transfers are made to other accounts, pass through Bitcoin mixers and tradedfor Monero and back in to Bitcoin using services like ShapeShift before being cashed out.
a.Describe the steps taken to create the malware and its related infrastructure.[5 marks] 网络犯罪代考
b.Describe 5 existing technical mitigation techniques or substantial challenges that the criminals have to overcome. [5 marks]
c.What 3 actions could users take to protect themselves from this cybercriminalC.operation? How likely do you think is it that this advice will be followed?[6 marks]
d.Design one economical mitigation against this criminal operation.[4 marks]
e.How could this cybercriminal operation be improved from the criminal’s perspective?e.[5 marks]
3.Dark web 网络犯罪代考
a.What are the differences between the surface web, the deep web, and the dark web?How can each ofthem be accessed?[3 marks]
b.What was the Silk Road? Describe the steps required to access it, buy goods from it, andpay for them?[7 marks]
c.What was the effect of the closure of the silk road?[2 marks]
d.What is a cryptocurrency?[2 marks]
e.How are transactions added to the bitcoin ledger?[4 marks] 网络犯罪代考
f.Discuss the anonymity properties of bitcoin.[7 marks]
4.Cybercrime mitigation
a.What are the five categories of situational crime prevention? For each of these, give anexample which could help to reduce cybercrime.[5 marks]
b.What are common implementation issues with mitigations against cybercrime?[4 marks]
c.To what extent do your examples from a) suffer from these implementation issues?[5 marks]
d.What are search engine optimisations? Discuss the role they play in criminal enterprises.[3 marks]
e.Discuss the effectiveness of mitigations against black hat SEOs.[8 marks]
更多代写:Psychology代写 多邻国助考 操作系统作业辅导 outline怎么写 reflective writing怎么写 论文怎么选题
合作平台:essay代写 论文代写 写手招聘 英国留学生代写